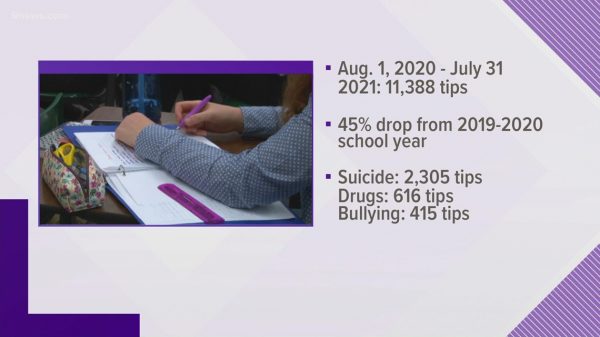
Ukraine’s Ministry of Protection and Armed Forces web sites and on-line providers of two state-owned banks had been disrupted by suspected cyberattacks on Tuesday, authorities and financial institution officers have stated.
The nation’s protection ministry stated in an English-language
Fb
publish that its internet portal suffered a probable distributed denial of service assault, through which hackers flooded the web site with site visitors to overload its programs and take it offline.
“Scheduled technical work is at present beneath approach on the restoration of the common functioning of the online portal of the Ministry of Protection of Ukraine,” the ministry stated, including it will share updates via social media.
DDoS incidents additionally disrupted internet providers of the Armed Forces of Ukraine and PrivatBank and Oschadbank, the nation’s largest lenders, in accordance with the State Service of Particular Communication and Info Safety of Ukraine. It stated in an announcement {that a} working group of Ukrainian cyber specialists “is taking all essential measures to withstand and localize the cyberattack.”
Safety specialists have warned in current weeks of cyberattacks concentrating on Ukrainian infrastructure as Russian troops mass on the nation’s border in what Western officers worry is a prelude to an invasion. U.S. and European officers additionally worry that the consequences of extra harmful hacking campaigns, reminiscent of assaults geared toward disabling pc networks or corrupting delicate information, might ripple throughout borders.

Kostiantyn Korsun, co-founder of the Ukrainian cyber agency Berezha Safety Group.
Picture:
Serhii Anishchenko/Zuma Press
Victor Zhora, chief digital transformation officer on the State Service of Particular Communication and Info Safety of Ukraine, stated it’s too early to attribute Tuesday’s incidents to a specific hacker or group. He additionally stated “the assault continues.”
The incident at PrivatBank spanned a number of hours, leaving providers together with automated teller machines down for an hour, a spokesman stated. Whereas the financial institution restored its providers, it nonetheless faces “instability” on its Privat24 cellular app and is working to safe its operations, the spokesman stated.
Representatives for Oschadbank, the opposite lender talked about by Ukrainian officers, didn’t instantly reply to a request for remark.
The White Home is conscious of the studies and has “reached out to Ukrainian counterparts to supply help within the investigation and response to those incidents,” a Nationwide Safety Council spokeswoman stated. She declined to remark additional.
It’s potential such assaults could possibly be carried out by Russian-linked hackers or opportunistic cybercriminals, stated Kostiantyn Korsun, co-founder of the Ukrainian cyber agency Berezha Safety Group. Prior to now, he stated, suspected Kremlin-linked cyberattacks have tried to sow confusion as a part of hybrid warfare towards Ukrainians within the japanese a part of the nation.
Final month, hackers defaced the web sites of dozens of Ukrainian authorities companies, whereas not less than two companies additionally found a probably extra harmful “wiper” malware meant to render pc programs inoperable. The Kremlin denied involvement within the incidents.
A disruption of presidency providers may be “very efficient as a result of it’s seen for hundreds of thousands of individuals on the identical second,” Mr. Korsun stated.
Officers within the U.S., U.Ok., Canada and elsewhere in current weeks have warned that cyberattacks linked to a Russian invasion of Ukraine might unfold throughout worldwide pc networks and disrupt infrastructure.
Final week, the U.S. Cybersecurity and Infrastructure Safety Company issued a “Shields Up” alert urging firms to replace their programs, impose multifactor authentication and extra aggressively monitor for uncommon exercise. Some U.S. firms have been taking such actions even when they don’t do enterprise in Ukraine.
“Whereas there should not at present any particular credible threats to the U.S. homeland, we’re aware of the potential for the Russian authorities to think about escalating its destabilizing actions in ways in which could affect others outdoors of Ukraine,” CISA stated.
U.S. and European firms ought to observe and be taught from Tuesday’s assaults and assume they’re state-backed, stated Christian Sorenson, a former cyberwarfare officer at U.S. Cyber Command who now runs safety firm SightGain Inc.
“Take a look at the methods that they’re utilizing, check these methods towards your infrastructure and just remember to’re blocking, detecting and responding to them, earlier than they’re used towards you,” he stated.
Some U.S. banks have been operating via contingency plans to arrange for Russia-linked incidents, stated Tim Eades, chief government of vArmour, a cybersecurity firm advising firms that embody monetary providers companies.
The monetary sector should adjust to tighter safety requirements than different sectors however “there’s clearly weaknesses in all issues in life,” Mr. Eades stated.
—James Rundle, Catherine Stupp and Nicolle Liu contributed to this text.
Write to David Uberti at david.uberti@wsj.com
Copyright ©2022 Dow Jones & Firm, Inc. All Rights Reserved. 87990cbe856818d5eddac44c7b1cdeb8